4년 전 거라 조금 수정이 필요한 부분이 있다.
키 교환의 Diffie-Hellman는 0000000000 으로
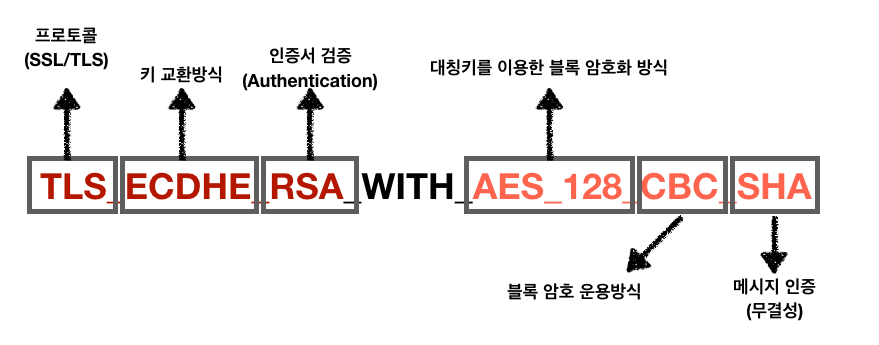
TLS 1.3의 출시로 SSL ROBOT이 주목되는지는 모르겠지만, 키 교환과 암호화 방식, 검증 방식에 대해 가장 잘 설명된 그림을 찾았다.
윈도우즈 설정 참고 사이트
https://support.microsoft.com/ko-kr/help/245030/how-to-restrict-the-use-of-certain-cryptographic-algorithms-and-protoc
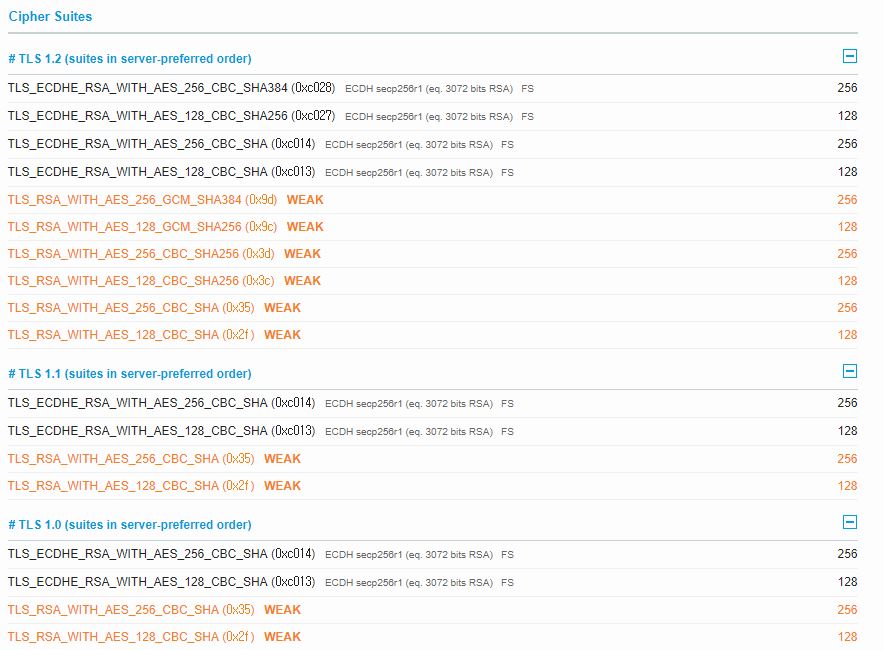
TLS 1.0과 RSA가 키교환 알고리즘으로 사용되는 서버의 예이다.
아래 파워쉘 스크립트를 이용해 설정을 보완할 수 있는데, 선택적으로 필요한 것을 적용하면, 취약점 제거에 용이할 것이다.
공개 키 암호 표준(Public-Key Cryptography Standard, PKCS)은 RSA 시큐리티에서 정한, 공개 키 암호에 대한 사용 방식에 대한 표준 프로토콜이다.
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELKeyExchangeAlgorithmsPKCS' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELKeyExchangeAlgorithmsPKCS' -name Enabled -value '0x00000000' -PropertyType 'DWord' -Force
$cipherSuitesOrder = @( 'TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P521', 'TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384', 'TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256', 'TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P521', 'TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P384', 'TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256', 'TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P521', 'TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P521', 'TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384', 'TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256', 'TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384', 'TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256', 'TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P521', 'TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384', 'TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P521', 'TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384', 'TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256', 'TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P521', 'TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P384', 'TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P521', 'TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P384', 'TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256', 'TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P521', 'TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P384', 'TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256', 'TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P521', 'TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P384', 'TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256','TLS_RSA_WITH_AES_256_CBC_SHA256','TLS_RSA_WITH_AES_256_CBC_SHA','TLS_RSA_WITH_AES_128_CBC_SHA256','TLS_RSA_WITH_AES_128_CBC_SHA')
$cipherSuitesAsString = [string]::join(',', $cipherSuitesOrder)
New-ItemProperty -path 'HKLM:SOFTWAREPoliciesMicrosoftCryptographyConfigurationSSL�0010002' -name 'Functions' -value $cipherSuitesAsString -PropertyType 'String' -Force | Out-Null
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Server' -name 'Enabled' -value '0x00000000' -PropertyType 'DWord' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force
기존 파워쉘 스크립트는 오래되어 수정이 필요하다.
https://gist.github.com/matejskubic/10268126
### http://www.hass.de/content/setup-your-iis-ssl-perfect-forward-secrecy-and-tls-12
# Add and Enable SSL 3.0 for client and server SCHANNEL communications
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0' -Force
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Server' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Server' -name 'Enabled' -value '0xffffffff' -PropertyType 'DWord' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force
# Add and Enable TLS 1.0 for client and server SCHANNEL communications
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0' -Force
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Server' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Server' -name 'Enabled' -value '0xffffffff' -PropertyType 'DWord' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force
# Add and Enable TLS 1.1 for client and server SCHANNEL communications
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1' -Force
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Server' -Force
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Client' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Server' -name 'Enabled' -value '0xffffffff' -PropertyType 'DWord' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Client' -name 'Enabled' -value 1 -PropertyType 'DWord' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force
# Add and Enable TLS 1.2 for client and server SCHANNEL communications
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2' -Force
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -Force
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -name 'Enabled' -value '0xffffffff' -PropertyType 'DWord' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -name 'Enabled' -value 1 -PropertyType 'DWord' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.2Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force
# Disable Multi-Protocol Unified Hello
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsMulti-Protocol Unified HelloServer' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsMulti-Protocol Unified HelloServer' -name Enabled -value 0 -PropertyType 'DWord' -Force
# Disable PCT 1.0
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsPCT 1.0' -Force
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsPCT 1.0Server' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsPCT 1.0Server' -name Enabled -value 0 -PropertyType 'DWord' -Force
# Disable SSL 2.0 (PCI Compliance)
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 2.0Server' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 2.0Server' -name Enabled -value 0 -PropertyType 'DWord' -Force
#DO NOT USE FOR NOW
#
# WARNING: Notice I didn't turn off SSL 3.0 - the reason for this is due to the fact that, like it or not,
# there are still people out there using Windows XP with IE 6/7. Without SSL 3.0 enabled, there would be
# no protocol for those people to fall back on.
# Disable SSL 3.0 (PCI Compliance)
#
#md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Server' -Force
#New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 3.0Server' -name Enabled -value 0 -PropertyType 'DWord' -Force
# Disable insecure ciphers
$insecureCiphers = 'NULL','RC2 40/128','RC2 56/128','RC2 128/128','RC4 40/128','RC4 56/128','RC4 64/128','DES 56/56'
Foreach ($insecureCipher in $insecureCiphers) {
$key = (Get-Item HKLM:).OpenSubKey('SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphers', $true).CreateSubKey($insecureCipher)
$key.SetValue('Enabled', 0, 'DWord')
$key.close()
Write-Host "$insecureCipher has been disabled"
}
# Enable new secure ciphers
$insecureCiphers = 'RC4 128/128','Triple DES 168/168','AES 128/128','AES 256/256'
Foreach ($insecureCipher in $insecureCiphers) {
$key = (Get-Item HKLM:).OpenSubKey('SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphers', $true).CreateSubKey($insecureCipher)
New-ItemProperty -path "HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELCiphers$insecureCipher" -name 'Enabled' -value '0xffffffff' -PropertyType 'DWord' -Force
$key.close()
Write-Host "$insecureCipher has been enabled"
}
# Set hashes configuration
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELHashesMD5' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELHashesMD5' -name Enabled -value '0xffffffff' -PropertyType 'DWord' -Force
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELHashesSHA' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELHashesSHA' -name Enabled -value '0xffffffff' -PropertyType 'DWord' -Force
# Set KeyExchangeAlgorithms configuration
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELKeyExchangeAlgorithmsDiffie-Hellman' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELKeyExchangeAlgorithmsDiffie-Hellman' -name Enabled -value '0xffffffff' -PropertyType 'DWord' -Force
md 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELKeyExchangeAlgorithmsPKCS' -Force
New-ItemProperty -path 'HKLM:SYSTEMCurrentControlSetControlSecurityProvidersSCHANNELKeyExchangeAlgorithmsPKCS' -name Enabled -value '0xffffffff' -PropertyType 'DWord' -Force
# Set cipher suites order as secure as possible (Enables Perfect Forward Secrecy)
New-ItemProperty -path 'HKLM:SOFTWAREPoliciesMicrosoftCryptographyConfigurationSSL�0010002' -name 'Functions' -value 'TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P521,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P521,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P384,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P521,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P521,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P521,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P521,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P521,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P384,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P521,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P384,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P521,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P384,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P521,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P384,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256,TLS_DHE_DSS_WITH_AES_256_CBC_SHA256,TLS_DHE_DSS_WITH_AES_256_CBC_SHA,TLS_DHE_DSS_WITH_AES_128_CBC_SHA256,TLS_DHE_DSS_WITH_AES_128_CBC_SHA,TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_RC4_128_SHA,TLS_RSA_WITH_3DES_EDE_CBC_SHA' -PropertyType 'String' -Force
Write-Host 'After the system has been rebooted you can verify your server configuration at https://www.ssllabs.com/ssltest/'
Write-Host -ForegroundColor Red 'A computer restart is required to apply settings. Restart computer now?'
Restart-Computer -Force -Confirm

















댓글 달기