

아래에 웹사이트, 캔버스 URL, MObile Web URL은 http://주소/facebook/ 로 모두 동일하게 적어도 된다.






[FACEBOOK] 앱 만들기2 - 담벼락에 글 쓰기, 글 가져오기, 생일 및 프로필 보기



[FACEBOOK] 앱 만들기2 - 담벼락에 글 쓰기, 글 가져오기, 생일 및 프로필 보기



[MAC LION] launchpad 아이콘 삭제
[OSX] VMWARE 에 WINDOWS 설치 후, 키보드 매핑
http://docs.cena.co.kr/?mid=textyle&category=13620&document_srl=17478
위 사이트를 참고하였다.
Left Option(0038) -> Left Windows(E05B)
Left Command(E05B) -> Left Alt(0038)
Right Control(E01D) -> Context Menu(E05D)
Right Option(E038) -> 한자(E071)
Right Command(E05C) -> 한글(E072)
위와 같이 변경해 보았으나, 기본적으로 Left Command + Tab이 OSX의 창 전환 기능이기 때문에, WINDOWS에서 사용할 수 없다. 그래서 HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlKeyboard Layout
에서 Scancode Map의 데이터를 다음과 같이 입력했다.
00 00 00 00 // Map Header
00 00 00 00 // Map Version
06 00 00 00 // Count (DWORD)
5B E0 5B E0 // Left Command(E05B) -> Left Windows(E05B)
38 00 38 00 // Left Option(0038) -> Left Alt(0038)
5D E0 1D E0 // Right Control(E01D) -> Context Menu(E05D)-> 내 맥북 AIR에는 없다
71 E0 38 E0 // Right Option(E038) -> 한자(E071)
72 E0 5C E0 // Right Command(E05C) -> 한글(E072)
00 00 00 00
이렇게 하여, 한자, 한글만 적용했다.
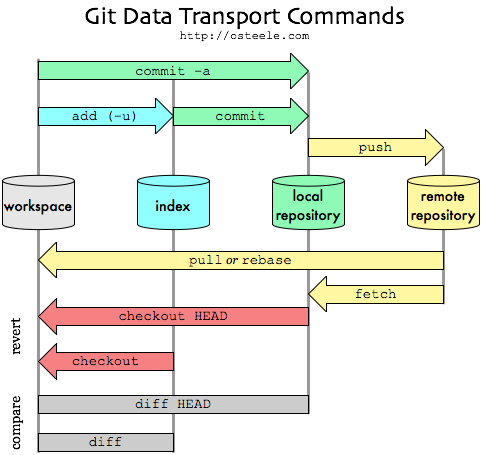
[GIT] github의 기본적인 명령어
[다음View] 외부게시글 이용해 등록하기
 이미, 블로그가 다음View 에 가입되어 있는데, 외부 게시판에서 등록하고 싶다면, 새로운 아이디를 만들어야 한다.
이미, 블로그가 다음View 에 가입되어 있는데, 외부 게시판에서 등록하고 싶다면, 새로운 아이디를 만들어야 한다.[Tip] Windows NT/2000/XP/2003/Vista 비밀번호 분실 해제









[XML] Dublin Core(DC)
| Dublin Core 15개 데이터 요소 | ||
| 콘텐츠 기술(내용) 요소 | 지적속성요소 | 물리적 기술(구현)요소 |
| Title(표제) Subject(주제) Description(설명) Source(출전) Language(언어) Relation(관련자료) Coverage(내용범위) | Creator(제작자) Publisher(발행처) Contributor(기타제작자) Right(이용조건) | Date(발행일자) Type(자료유형) Format(형식) Identifier(식별자) |
[PPT] 파워포인트 전체 페이지 넣는 VBA 스크립트

[WCAG] 플래시 대체 텍스트
터보코드
melfb.m
function m = melfb(p, n, fs)
p=9;
n=2048;
fs=2000;
f0 = 700 / fs;
fn2 = floor(n/2);
lr = log(1 + 0.5/f0) / (p+1);
% convert to fft bin numbers with 0 for DC term
bl = n * (f0 * (exp([0 1 p p+1] * lr) - 1));
b1 = floor(bl(1)) + 1;
b2 = ceil(bl(2));
b3 = floor(bl(3));
b4 = min(fn2, ceil(bl(4))) - 1;
pf = log(1 + (b1:b4)/n/f0) / lr;
fp = floor(pf);
pm = pf - fp;
r = [fp(b2:b4) 1+fp(1:b3)];
c = [b2:b4 1:b3] + 1;
v = 2 * [1-pm(b2:b4) pm(1:b3)];
m = sparse(r, c, v, p, 1+fn2);
size_m = size(m);
plot(linspace(0, (fs/2), (n/2)+1),m);
%title('Mel-scale filter bank');
xlabel('Frequency (Hz)');
set(get(gca,'xlabel'),'FontSize',20);
ylabel('Amplitude');
set(get(gca,'ylabel'),'FontSize',20);
set(gca, 'XTick',[0:100:2000], 'XTickLabel',[0:100:1000],'fontsize',20);
set(gca, 'YTick',[0:1:2], 'YTickLabel',[0:1:2],'fontsize',20);
Hamming Window Amplitude Response
% Chapter 7: Hamming Window Amplitude Response
%
M = 45; alpha = (M-1)/2;
n = -alpha:alpha;
w = (hamming(M))'; sumw = sum(w);
N = 1000; omega = (2*pi/N)*[-N/2:N/2];
Wr = real(w*(exp(-j*n'*omega)));
db = 20*log10(abs(Wr)/max(Wr));
IntWr = cumsum(Wr);
Intdb = 20*log10(abs(IntWr)/N);
k = (N/2+1) - min(find(Intdb > -53));
tr_width = 2*k*2*M/N, %actual transition width in pi/M units
omega1 = -(tr_width/2)/M; omega2 = (tr_width/2)/M;
%
% plots
subplot(1,1,1)
subplot(2,2,1); stem(n,w);
axis([-(alpha+8),(alpha+8),-0.1,1.1]);
set(gca,'YTickMode','manual','YTick',[0,1])
set(gca,'XTickMode','manual','XTick',[-22,0,22]);
title('Hamming Window : M=45')
xlabel('n'); ylabel('w(n)')
subplot(2,2,3); plot(omega/pi,Wr);
axis([-1,1,-2,sumw+5]);
set(gca,'YTickMode','manual','YTick',[0,sumw])
set(gca,'XTickMode','manual','XTick',[-1,0,1]); grid
set(gca,'XTickLabelMode','manual','XTickLabels',[' 0';'22';'45']);
title('Amplitude Response')
xlabel('frequency in pi units'); ylabel('Wr')
subplot(2,2,2); plot(omega/pi,db);
axis([-1,1,-60,10]);
set(gca,'YTickMode','manual','YTick',[-60,-42,0])
set(gca,'YTickLabelMode','manual','YTickLabels',['60';'43';' 0'])
set(gca,'XTickMode','manual','XTick',[-1,0,1]);grid
title('Amplitude Response in dB')
xlabel('frequency in pi units'); ylabel('Decibels')
subplot(2,2,4); plot(omega/pi,Intdb);
axis([-1,1,-70,10]);
set(gca,'YTickMode','manual','YTick',[-70,-54,0])
set(gca,'YTickLabelMode','manual','YTickLabels',['70';'54';' 0'])
set(gca,'XTickMode','manual','XTick',[-1;omega1;omega2;1]);grid
set(gca,'XTickLabelMode','manual','XTickLabels',['-1';' ';' ';' 1'])
title('Accumulated Amplitude Response')
xlabel('frequency in pi units'); ylabel('Decibels')
text(omega2,5,'Width=(6.6)*pi/M')
travelling salesman problem
|
flex 외부 변수 이용, 받기, 현재 url
json encoding, decoding
댓글 달기